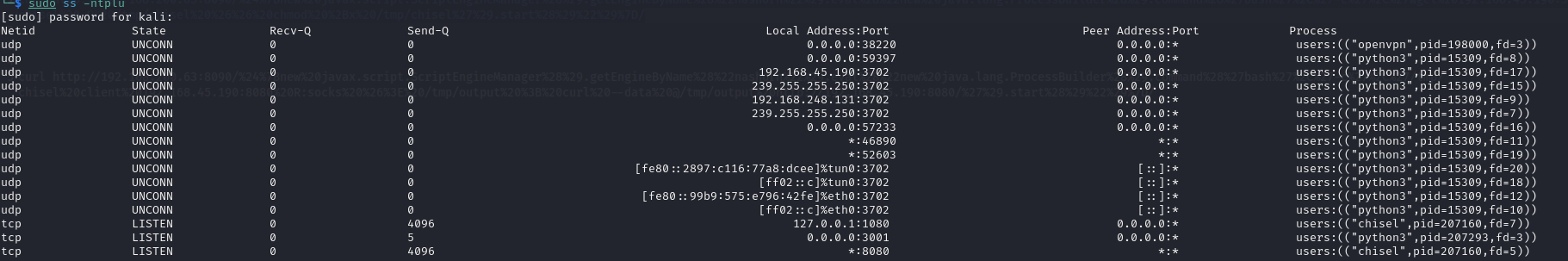
Port Forwarding and Tunneling

实用的Windows及Linux端口转发/内网横向移动技巧。
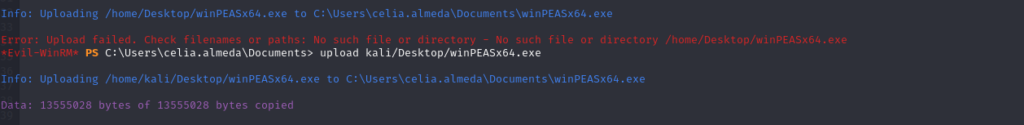
Lateral Movement




AD域横向移动基础
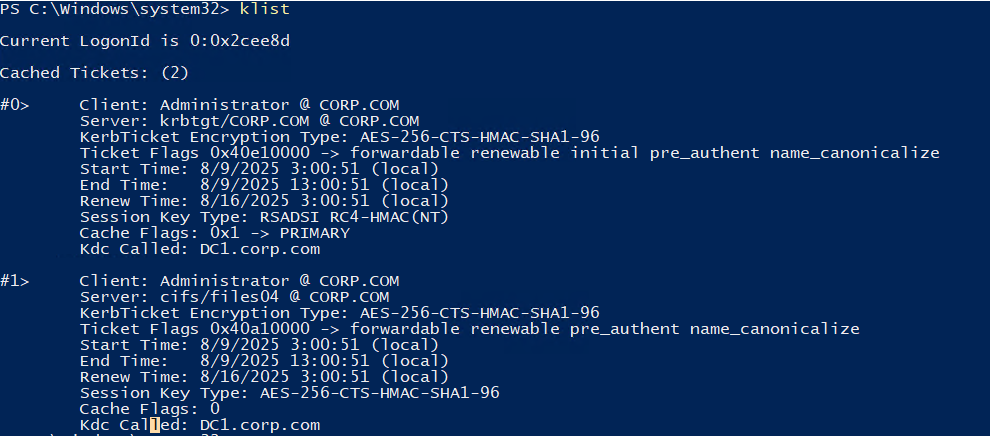
Active Directory基础攻击策略
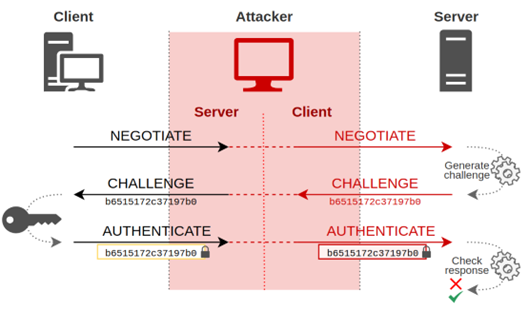
各种服务及Windows NTLM的密码攻击

Windows系统基础水平及垂直权限提升
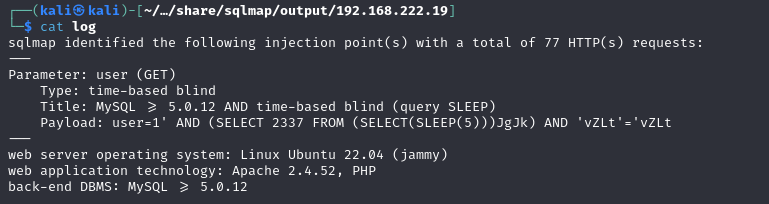
SQL Injection
File Inclusion & Directory Traversal

SQL注射攻击
基本网站目录遍历攻击

File Upload
利用Web应用的文件上传功能漏洞实现远程代码执行。